

|
|
Patents
|
Publications
List by publication type:
Steven Noel, Eric Harley, Kim Ham Tam, Michael Limiero, Matt Share, "CyGraph: Graph-Based Analytics and Visualization for Cybersecurity," in Cognitive Computing: Theory and Applications, Handbook of Statistics 35, V. Raghavan, V. Gudivada, V. Govindaraju, C.R. Rao (eds.), Elsevier, 2016. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Sushil Jajodia, Steven Noel, "Topological Vulnerability Analysis," in Cyber Situational Awareness: Issues and Research, Advances in Information Security 46, S. Jajodia, P. Liu, V. Swarup, C. Wang (eds.), Springer, 2010. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, "Proactive Intrusion Prevention and Response via Attack Graphs," in Practical Intrusion Analysis: Prevention and Detection for the Twenty-First Century, R. Trost (ed.), Addison-Wesley Professional, 2009. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Sushil Jajodia, Steven Noel, "Topological Vulnerability Analysis: A Powerful New Approach for Network Attack Prevention, Detection, and Response," in Algorithms, Architectures, and Information Systems Security, B. Bhattacharya, S. Sur-Kolay, S. Nandy, and A. Bagchi (eds.), World Scientific Press, 2007. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Sushil Jajodia, Steven Noel, Brian O'Berry, "Topological Analysis of Network Attack Vulnerability," in Managing Cyber Threats: Issues, Approaches and Challenges, V. Kumar, J. Srivastava, A. Lazarevic (eds.), Springer, 2005. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Steven Noel, Vijay Raghavan, C.-H. Henry Chu, "Document Clustering, Visualization, and Retrieval via Link Mining," in Clustering and Information Retrieval, W. Wu, H. Xiong, and S. Shekhar (eds.), Springer, 2003. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Steven Noel, Duminda Wijesekera, Charles Youman, "Modern Intrusion Detection, Data Mining, and Degrees of Attack Guilt," in Applications of Data Mining in Computer Security, D. Barbara and S. Jajodia (eds.), Springer, 2002. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, "Wavelets and Neural Networks for Radar," in Progress in Unsupervised Learning of Artificial Neural Networks and Real-World Applications, Russian Academy of Nonlinear Sciences, ISBN 0-620-23629-9, 1998. ![]()
![]() Chapter
Chapter ![]()
![]() Citations
Citations
Lingyu Wang, Sushil Jajodia, Anoop Singhal, Pengsu Cheng, Steven Noel, "k-Zero Day Safety: A Network Security Metric for Measuring the Risk of Unknown Vulnerabilities," IEEE Transactions on Dependable and Secure Computing, 2013. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, Lingyu Wang, Anoop Singhal, "Measuring Security Risk of Networks Using Attack Graphs," International Journal of Next-Generation Computing, Vol. 1, No. 1, July 2010. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, "Optimal IDS Sensor Placement and Alert Prioritization Using Attack Graphs," Journal of Network and Systems Management, special issue on Security Configuration Management, acceptance ratio 4/27, September 2008. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
Lingyu Wang, Steven Noel, Sushil Jajodia, "Minimum-Cost Network Hardening Using Attack Graphs," Computer Communications, 29(18), 3812-3824, November 2006. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
Harold Szu, Steven Noel, Seong-Bin Yim, Jeff Willey, Joe Landa, "Multimedia Authenticity Protection with ICA Watermarking and Digital Bacteria Vaccination," Neural Networks, 16(5-6), special issue for top 10% papers from the 2003 International Joint Conference on Neural Networks, 907-914, 2003. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
Steven Noel, C.-H. Henry Chu, Vijay Raghavan, "Co-Citation Count versus Correlation for Influence Network Visualization," Information Visualization, 2(3), 2003. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, "Proximity Sensing with Wavelet-Generated Video," Journal of Electronic Imaging, 7(4), October 1998. ![]()
![]() Article
Article ![]()
![]() Citations
Citations
William Heinbockel, Steven Noel, James Curbo, "NATO RFI Mission Modeling," NATO Cyber Defence Situational Awareness Solutions Demonstration, Mons, Belgium, November, 2016. ![]()
![]() Paper
Paper
William Heinbockel, Steven Noel, James Curbo, "Mission Dependency Modeling for Cyber Situational Awareness," NATO IST-148 Symposium on Cyber Defence Situation Awareness, Sofia, Bulgaria, October, 2016. ![]()
![]() Paper
Paper
Steven Noel, "CyGraph: Big Data Analytics for Network Attack Mapping," GraphConnect, San Francisco, California, October, 2015. ![]() Blog
Blog ![]() Video
Video
Steven Noel, William Heinbockel, "An Overview of MITRE Cyber Situational Awareness Solutions," NATO Cyber Defence Situational Awareness Solutions Conference, Bucharest, Romania, August, 2015. ![]()
![]() Paper
Paper
Steven Noel, Jackson Ludwig, Prem Jain, Dale Johnson, Roshan K. Thomas, Jenny McFarland, Ben King, Seth Webster, Brady Tello, "Analyzing Mission Impacts of Cyber Actions (AMICA)," Best Paper award, NATO IST-128 Workshop on Cyber Attack Detection, Forensics and Attribution for Assessment of Mission Impact, Istanbul, Turkey, June, 2015. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Eric Harley, Kam Him Tam, Greg Gyor, "Big-Data Architecture for Cyber Attack Graphs: Representing Security Relationships in NoSQL Graph Databases," IEEE Symposium on Technologies for Homeland Security (HST), Boston, Massachusetts, April, 2015. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, "Interactive Visualization and Text Mining for the CAPEC Cyber Attack Catalog," ACM IUI Workshop on Visual Text Analytics, Atlanta, Georgia, March, 2015. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Jeffrey Jenkins, Charles Sweet, James Sweet, Steven Noel, Harold Szu, "Authentication, Privacy, Security can Exploit Brainwave by Biomarker," Independent Component Analyses, Compressive Sampling, Wavelets, Neural Net, Biosystems, and Nanoengineering XII, SPIE - The International Society for Optical Engineering, Baltimore, Maryland, May 2014. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, "Metrics Suite for Network Attack Graph Analytics," 9th Annual Cyber and Information Security Research Conference (CISRC), Oak Ridge National Laboratory, Tennessee, April 2014. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, "Metrics Suite for Network Attack Graphs," 65th Meeting of IFIP Working Group 10.4 on Dependable Computing and Fault Tolerance, Sorrento, Italy, January, 2014. ![]()
![]() Presentation
Presentation
Massimiliano Albanese, Sushil Jajodia, Steven Noel, "Time-Efficient and Cost-Effective Network Hardening Using Attack Graphs," 42nd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Boston, Massachusetts, June 2012. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Sushil Jajodia, Steven Noel, Pramod Kalapa, Massimiliano Albanese, John Williams, "Cauldron: Mission-Centric Cyber Situational Awareness with Defense in Depth," 30th Military Communications Conference (MILCOM), Baltimore, Maryland, November 2011. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
John Williams, Pramod Kalapa, Steven Noel, "Topological Vulnerability Analysis -- Automatically Predicting Possible Paths of Cyber Attack," 10th Annual Air Force Intelligence, Surveillance, and Reconnaissance (ISR) Agency Communications and Information Conference, San Antonio, Texas, November 2010.
Lingyu Wang, Sushil Jajodia, Anoop Singhal, Steven Noel, "k-Zero Day Safety: Measuring the Security Risk of Networks against Unknown Attacks," European Symposium on Research in Computer Security (ESORICS), Athens, Greece, September 2010. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, "Cauldron -- Network Assessment Tool Demonstration," 9th Annual Air Force Intelligence, Surveillance, and Reconnaissance (ISR) Agency Communications and Information Conference, San Antonio, Texas, January 2010. ![]()
![]() Paper
Paper
Steven Noel, Sushil Jajodia, "Advanced Vulnerability Analysis and Intrusion Detection through Predictive Attack Graphs," Critical Issues in C4I, Armed Forces Communications and Electronics Association (AFCEA) Solutions Series, Lansdowne, Virginia, May 2009. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Matthew Elder, Sushil Jajodia, Pramod Kalapa, Scott O'Hare, Kenneth Prole, "Advances in Topological Vulnerability Analysis," Cybersecurity Applications & Technology Conference For Homeland Security (CATCH), Washington, DC, March 2009. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Scott O'Hare, Steven Noel, Kenneth Prole, "A Graph-Theoretic Visualization Approach to Network Risk Analysis," Workshop on Visualization for Computer Security, Cambridge, Massachusetts, September 2008. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, "Attack Graphs for Sensor Placement, Alert Prioritization, and Attack Response," Cyberspace Research Workshop, Air Force Cyberspace Symposium, Shreveport, Louisiana, November 2007. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
J. Kendree Williams, Louis Rader, Darich Runyan, Sushil Jajodia, Steven Noel, "A Method for Automatic Course of Action Generation," Phoenix Challenge Conference, Baltimore, Maryland, February 2006.
Steven Noel, Sushil Jajodia, "Understanding Complex Network Attack Graphs through Clustered Adjacency Matrices," 21st Annual Computer Security Applications Conference (ACSAC), Tucson, Arizona, December 2005. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Michael Jacobs, Pramod Kalapa, Sushil Jajodia, "Multiple Coordinated Views for Network Attack Graphs," Workshop on Visualization for Computer Security (VizSec), Minneapolis, Minnesota, October 2005. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Eric Robertson, Sushil Jajodia, "Correlating Intrusion Events and Building Attack Scenarios through Attack Graph Distances," 20th Annual Computer Security Applications Conference (ACSAC), Tucson, Arizona, December 2004. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, "Managing Attack Graph Complexity through Visual Hierarchical Aggregation," ACM CCS Workshop on Visualization and Data Mining for Computer Security, Fairfax, Virginia, October 2004. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Sushil Jajodia, Brian O'Berry, Michael Jacobs, "Efficient Minimum-Cost Network Hardening via Exploit Dependency Graphs," 19th Annual Computer Security Applications Conference (ACSAC), Las Vegas, Nevada, December 2003. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Harold Szu, Steven Noel, Seong-Bin Yim, Jeff Willey, Joe Landa, "Protecting Multimedia Authenticity with ICA Vaccination of Digital Bacteria Watermarks," International Joint Conference on Neural Networks, Portland, Oregon, July 2003. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Ronald Ritchey, Brian O'Berry, Steven Noel, "Representing TCP/IP Connectivity for Topological Analysis of Network Security," in 18th Annual Computer Security Applications Conference (ACSAC), Las Vegas, Nevada, December 2002. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, C.-H. Henry Chu, Vijay Raghavan, "Visualization of Document Co-Citation Counts," 6th International Conference on Information Visualization, London, England, July 2002. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Brian O'Berry, Charles Hutchinson, Sushil Jajodia, Lynn Keuthan, and Andy Nguyen, "Combinatorial Analysis of Network Security," 16th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 2002. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Seong-Bib Yim, Steven Noel, Harold Szu, "Detecting Electrocardiogram Abnormalities with Independent Component Analysis," 15th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 2001. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Vijay Raghavan, C.-H. Henry Chu, "Visualizing Association Mining Results through Hierarchical Clusters," First IEEE International Conference on Data Mining, San Jose, California, November 2001. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, "Multimedia Authenticity with ICA Watermarks," 14th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 2000. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, Nian-Feng Tzeng, Chee-Hung Henry Chu, Santipong Tanchatchawal, "Video Compression with Embedded Wavelet Coding and Singularity Maps," 13th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 1999. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Yogesh Gohel, Steven Noel, Harold Szu, "Wavelets and Neural Networks for Radar Proximity Fuzing," 12th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 1998.
Addison Jump, Harold Szu, Steven Noel, "Characterization of Polynomials Satisfying the Super-Haar Condition," 12th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 1998. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, "Doppler Frequency Estimation with Wavelets and Neural Networks," 12th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 1998. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, "Multiple-Resolution Clustering for Recursive Divide and Conquer," 11th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 1997. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, Yogesh Gohel, "Wavelet Detection of Singularities in the Presence of Fractal Noise," 11th Annual International Symposium on Aerospace/Defense Sensing, Simulation, and Controls (AeroSense), Orlando, Florida, April 1997. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, Harold Szu, "Multiple-Resolution Divide and Conquer Neural Networks for Large Scale TSP-Like Problems," International Conference on Neural Networks, Houston, Texas, July 1997. ![]()
![]() Paper
Paper ![]()
![]() Citations
Citations
Steven Noel, "Integrated Process/Graphical Modeling and Simulation for Assessing Cyber Impacts on Missions," Military Operations Research Society (MORS) Emerging Techniques Special Meeting, Alexandria, Virginia, December, 2016.
Steven Noel, "Behavioral Analytics via Graph Methods within a Cyber Resilience Framework," Army Network Enterprise Technology Command (NETCOM) Command Strategy Group Meeting, Sierra Vista, Arizona, November, 2016.
Steven Noel, "CyGraph: Graph Analytics for Cybersecurity," booth demonstration, International Conference for Military Communications (MILCOM), Baltimore, Maryland, November, 2016.
Steven Noel, "NoSQL Graph Databases for Cybersecurity Analytics," Marine Forces Cyber Command (MARFORCYBER) Symposium on Analyic Clouds, Quantico, Virginia, October, 2016.
Steven Noel, "CyGraph: Graph-Based Analytics and Visualization for Cybersecurity," MITRE NSEC R&T Committee Meeting, McLean, Virginia, October, 2016.
Steven Noel, CyGraph Project Overview, MITRE NSEC R&T Committee Meeting, McLean, Virginia, April 2016.
Steven Noel, "Graph Analytics and Visualization for Cybersecurity," Hanscom Innovation Exchange, Hanscom Air Force Base, Massachusetts, April 2016.
Dale Johnson, Steven Noel, "Cyber Situational Awareness and Cyber Threat Modeling - A MITRE Perspective," Cyber Modeling and Simulation Technical Working Group (Cyber Threat Modeling Subgroup), DoD Modeling and Simulation Coordination Office, Alexandria, Virginia, December, 2015.
Steven Noel, "CyGraph - Briefing and Demonstration," 24th Air Force Cyber Technologies Demonstration, San Antonio, Texas, December, 2015.
Kam Him Tam, Steven Noel, "Overview of CyGraph: Big-Data Analytics for Network Attack Mapping," MITRE Naval Portfolio Innovation Exchange, McLean, Virginia, August, 2015.
Jackson Ludwig, Steven Noel, "Analyzing Mission Impacts of Cyber Actions (AMICA)," MITRE Cyber Security Modeling and Simulation Brown Bag, McLean, Virginia, August, 2015.
Steven Noel, "CyGraph: Big Data Analytics for Network Attack Mapping," MITRE Innovation Exchange on Software Defined Networking, Annapolis Junction, Maryland, June, 2015.
Steven Noel, Sushil Jajodia, "Metrics Suite for Enterprise-Level Attack Graph Analysis," DHS Cyber Security Division (CSD) Principal Investigators Meeting, Washington, DC, September, 2013.
Steven Noel, Sushil Jajodia, "Proposed Metrics Suite for Enterprise-Level Attack Graph Analysis," DHS Cyber Security Division (CSD) Principal Investigators Meeting, Washington, DC, October, 2012. ![]()
![]() Presentation
Presentation
Steven Noel, "Center for Secure Information Systems at George Mason University," National Centers of Academic Excellence in Information Assurance Education and Research Principal Investigators Meeting, Saint Louis, Missouri, November, 2010.
Steven Noel, Anup Ghosh, Sushil Jajodia, Angelos Stavrou, "Mapping Attack Paths in Black-Box Networks through Passive Vulnerability Inference," AFOSR Information Operations and Security Annual Review, Arlington, Virginia, July 2010.
Oscar Fuster, John Williams, Steven Noel, Aaron Stillwell, "CAULDRON Webinar," Epok, Inc., Bethesda, Maryland, March 2009.
Sushil Jajodia, Steven Noel, "Review of CAULDRON Tool," NSA, Linthicum, Maryland, March 2009.
Sushil Jajodia, Steven Noel, "Review of Topological Vulnerability Analysis," ARO Cyber Situational Awareness Workshop, Fairfax, Virginia, March 2009.
Steven Noel, Sushil Jajodia, Anup Ghosh, "Mapping Attack Paths in Black-Box Networks through Passive Vulnerability Inference," Mapping Cyber Assets to the Critical Missions They Support, AFRL Workshop, Johns Hopkins University Applied Physics Laboratory, Laurel, Maryland, February 2009.
Steven Noel, "CAULDRON Technology Review," Briefing to City of Seattle Chief Technology Officer, Seattle, Washington, December 2008.
Steven Noel, Anup Ghosh, "CAULDRON Network Attack Prediction And Defense," Briefing to US Senate Arms Committee Staff, December 2008.
Steven Noel, Pramod Kalapa, "CAULDRON Network Security Tool," Mid-Atlantic Innovation Showcase, McLean, Virginia, November 2008.
Steven Noel, "Center for Secure Information Systems at George Mason University," National Centers of Academic Excellence in Information Assurance Education and Research Principal Investigators Meeting, Phoenix, Arizona, October, 2008.
Steven Noel, Sushil Jajodia, Pramod Kalapa, "Combinatorial Analysis Utilizing Logical Dependencies Residing On Networks (CAULDRON)," 2008 DHS System Integrator Forum, Arlington, Virginia, February 2008.
Sushil Jajodia, Steven Noel, "Topological Analysis of Network Attack Vulnerability," NIST Seminar, Gaithersburg, Maryland, February 2008.
Steven Noel, "Window on Emerging Technology: Topological Vulnerability Analysis," US Secret Service Electronic Crimes Task Force Meeting, Miami, Florida, February 2007.
Steven Noel, "Enhanced Topological Vulnerability Analysis and Visualization," 3rd Annual AFRL Cyber Situational Awareness Collaboration Meeting, Fairfax, Virginia, April 2006.
Steven Noel, "Visualizing Network Attack Graphs," 2006 Information Assurance and Cyber Security Symposium, North Carolina A&T State University, Greensboro, North Carolina, March 2006.
Steven Noel, "Managing CAULDRON Attack Graph Complexity Through Hierarchical Aggregation," 2nd Annual AFRL Cyber Situational Awareness Collaboration Meeting, Fairfax, Virginia, April 2005.
Steven Noel, "Secure Information Infrastructure Protection through Topological Vulnerability Analysis," 84th Annual Meeting of the Transportation Research Board of the National Academies, Washington, DC, January 2005.
Steven Noel, "Using Efficient Attack Graphs to Automate Penetration Testing," Mitre Brownbag Seminar, McLean, Virginia, May 2004.
Steven Noel, "Network Penetration Analysis," AFRL Cyber Situational Awareness Collaboration Meeting, Fairfax, Virginia, April 2004.
Brian O'Berry, Steven Noel, Charles Hutchinson, Sushil Jajodia, "Topological Vulnerability Analysis," NSA Information Assurance Working Symposium, Tampa, Florida, July 2002.
Steven Noel, "Architecture for Topological Vulnerability Analysis," Annual Weapons Control Technology Symposium, The Johns Hopkins University Applied Physics Laboratory, Laurel, Maryland, June 2002.
Neil Johnson, Robert Weierbach, Brian O'Berry, Steven Noel, Charles Youman, "Information Assurance Products: Research and Test Results," E-Gov Information Assurance Conference, Washington, DC, December 2001.
Steven Noel, "Advanced Approaches to Network Vulnerability Analysis," DISA/NRL/NSA Workshop on Optical and Protocol Vulnerability Assessment in Fiber Optic Communication Networks, McLean, Virginia, May 2001.
Anup Ghosh, Steven Noel, Sushil Jajodia, Mapping Attack Paths in Black-Box Networks through Passive Vulnerability Inference, Technical Report AFRL-OSR-VA-TR-2012-0243, Air Force Research Laboratory, August 2011. ![]()
![]() Report
Report ![]()
![]() Citations
Citations
Sushil Jajodia, Steven Noel, Advanced Cyber Attack Modeling, Analysis, and Visualization, Technical Report AFRL-RI-RS-TR-2010-078, Air Force Research Laboratory, March 2010. ![]()
![]() Report
Report ![]()
![]() Citations
Citations
Sushil Jajodia, Steven Noel, Integration of Audit Data Analysis and Mining Techniques into AIDE, Technical Report AFRL-IF-RS-TR-2006-250, Air Force Research Laboratory, July 2006. ![]()
![]() Report
Report
Steven Noel, Vijay Raghavan, C.-H. Henry Chu, "Clustering and Visualizing Retrieval Output with Higher-Order Co-Citations," paper contest winner, IEEE Student Chapter, University of Louisiana, May 2001.
Steven Noel, Data Mining and Visualization of Reference Associations: Higher Order Citation Analysis, Ph.D. dissertation, University of Louisiana, Fall 2000. ![]()
![]() Manuscript
Manuscript ![]()
![]() Citations
Citations
Steven Noel, Wavelet Transforms for Radar Proximity Fuzing, M.S. Thesis, University of Louisiana, Fall 1998.
Steven Noel, Construction of the MK5A Star Catalog, technical report, Naval Surface Warfare Center, Dahlgren, Virginia, 1996.
Mathew Zuraski, Steven Noel, Video Demonstration for NATO Seasparrow Low-Light-Level Television, technical report, Naval Surface Warfare Center, Dahlgren, Virginia, 1991.
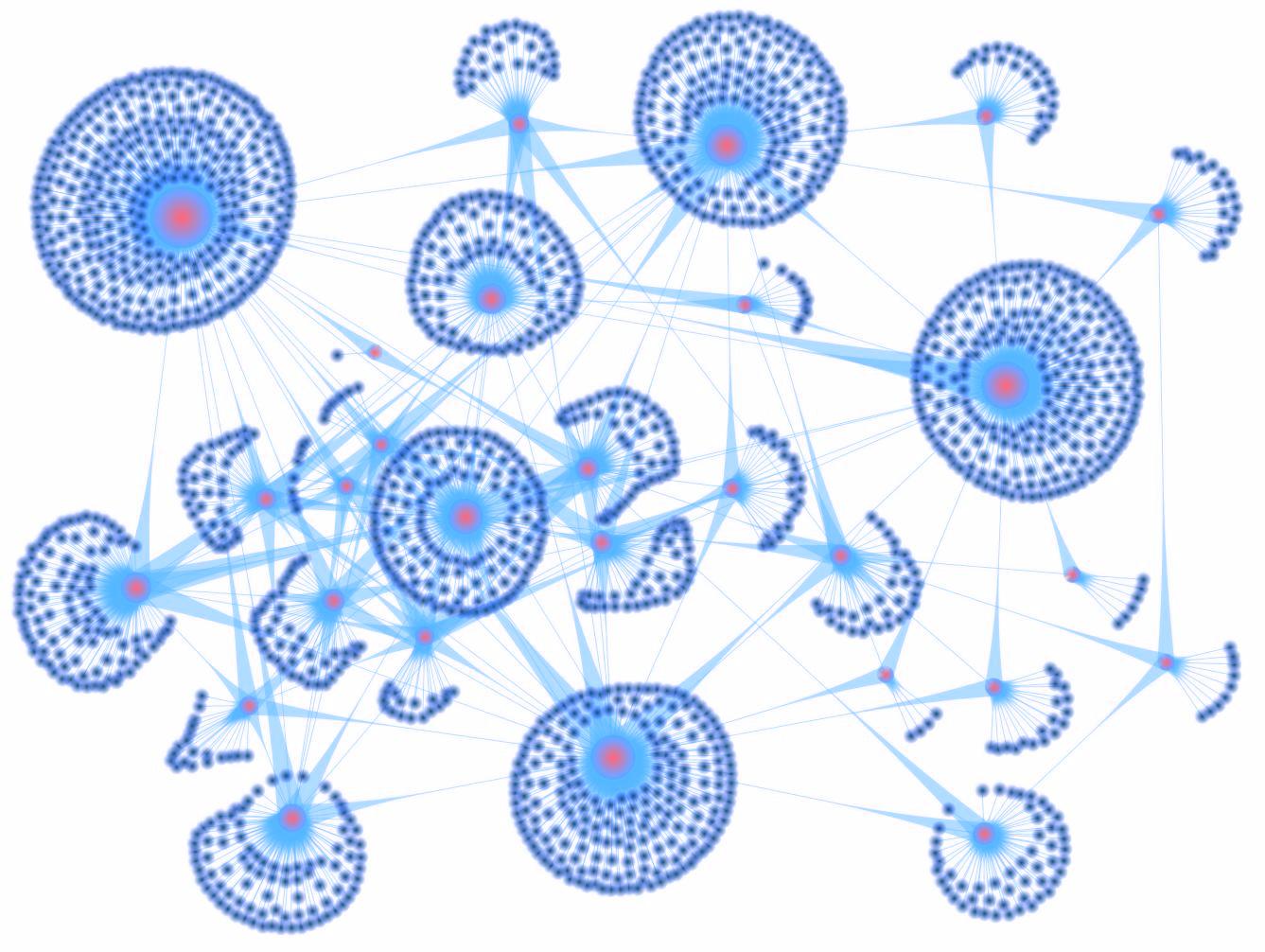
Here is a graph (as of January 19, 2016) of literature citations for selected papers. Citation direction is indicated by the width of edges (narrow is citing paper, wide is paper being cited). My papers are red nodes, others are blue nodes.
|
You can also search for my publications on various bibliography servers and digital libraries:
|
|
|
Patents
|
|||||||||||||||
|
|